News
What you need to know about doing business in the cloud
Small and medium-sized businesses are increasingly turning to offsite computer services for their IT needs. Utilization of the so-called “cloud” for both file storage and backup, as well as for web-based software (also know as software as a service or SaaS), is...
Senior care facilities have high cyber liability
As the nation’s baby boomers age, retirement communities and nursing homes are expanding. These senior living facilities often emphasize physical security as one of the main benefits they can provide to potential residents and their concerned families. Frequently,...
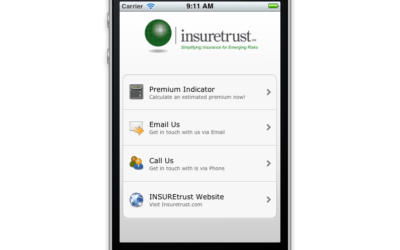
iPhone Premium Indicator App
INSUREtrust has just released its Premium Indicator application for the iPhone. In what is believed to be a first-of-its-kind mobile tool in the cyber liability industry, the app generates a range of potential premiums for two deductible amounts, after users answer...
Lessons learned from LinkedIn breach
As you may have heard by now, LinkedIn notified its users last week that it had been hacked. Out of about 150 million users, approximate 6 million had their passwords stolen and posted on a hacker web site. The breach of the social networking giant should come as no...
How secure are your company’s passwords?
Passwords are worth their weight in gold to hackers. Once a cyber criminal figures out an employee’s password, he has an entry into the company network. From that point, using other tools, the hacker can steal just about anything he wants, and wreak havoc in the...
Cyber crooks use clever techniques to trick honest employees and steal data
Hackers have a variety of ways to unleash cyber attacks on individuals and businesses, and they use their nefarious toolbox each and every day to steal sensitive information. According to Symantec’s 2011 Cybercrime Report, the daily cost of hacking in the US is a...
FEMA: Government, businesses vulnerable to cyber attacks
The nation is woefully unprepared for a major cyber attack, according to a new report released by the Federal Emergency Management Agency (FEMA). Among 31 core capabilities identified as key for disaster responsiveness, cyber security came in dead last, with a...
Attorneys face numerous cyber threats
When it comes to cyber risks, attorneys are often found litigating on behalf of clients who have been crime victims and are suing the company that the criminals hacked. However, sometimes, attorneys themselves fall victim to cyber criminals. Like any other business,...
CISPA: Turning Facebook and Google into government spies?
In what’s being called “Cyber Week” by some, Congress is focusing its attention on the highly complex problem of cyber security this week. Lawmakers are considering numerous measures to combat cyber terrorism and cyber theft. The bill getting the most attention is...
Companies collecting personally identifiable information might be breaking laws
How much of your personal information should a merchant be allowed to collect? What information does a merchant have a right to gather from you when you pay with a credit card? Should a merchant be barred from obtaining your zip code on the grounds that it is...
Newsletter Sign Up
Please fill out the form below to receive a quote from one of our specialists. If you need immediate assistance, please call us at 1-888-932-7475.